Hacker Techniques,
Tools, and
Incident Handling
Cryptographic Concepts
Were you able to understand this? It is a simple word that we hear every day. This is the word "WELCOME!"
WELCOME becomes ZHOFRPH when we replace each letter in this word by a letter that is three letters to the right of the original letter in the English alphabet. So, W becomes Z, E becomes H, and so on. To understand why we have done this, click the following questions. Next, click the ACTIVITY button to attempt a simple exercise.
- What is encryption?
- What is cryptography?
- What is asymmetric and symmetric encryption?
- What are the features of strong and weak encryption?
- How is encryption used for maintaining security?
- Which tools are available for encryption?






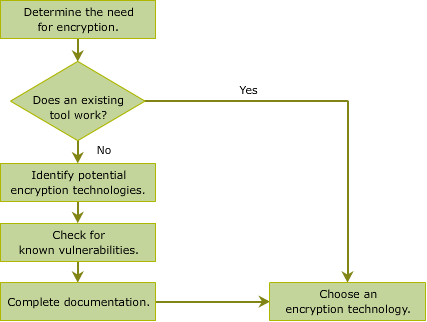
The following flowchart can be used to select an encryption technology to secure any communication over a network. After going through the flowchart, click the ACTIVITY button to attempt a simple activity on the encryption selection process.
- Security analyst
- Security manager
- Chief information security officer (CISO)
- End users

Click the following questions to learn more about the importance of encryption in maintaining security over a network. Next, click the ACTIVITY button to attempt an exercise.
- What are the benefits of encryption?
- What are the requirements that a security analyst needs to fulfill to use encryption effectively?


In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Following the instructions provided in the Lab Manual, you will be able to practice the steps IT Security Specialists perform on a daily basis and develop the skills required for effective execution and management of IT Security operations.
On a busy Wednesday morning, you are called for a meeting with the chief security officer, Mac. In the meeting, he says that he has some important tasks for you. Click the image of the chief security officer to get his instructions.
After you have gone through the challenge, navigate to Contributing Factors from the panel at the top of your screen.
I have called this meeting to give you an important task. Yesterday, I came to know that a significant vulnerability has been discovered in our university’s cryptosystem. This is a serious matter and can negatively affect the security of the data and applications being run at our offices. That is why I want you to do some research and come up with a list of things that the university should do to handle the situation.
You can ask the experts at the university about how our university uses the cryptosystem. I am also available for help and guidance if you need.
At the end of your research, I would like you to present a report on the threat the university faces and what it should do about the vulnerability. I would like you to explain what effect any changes required might have on the university or its students, employees, graduates, or other populations. The summary should include what the vulnerability is, how dangerous it could be, what its effects are, and how it can be countered. You should address communication regarding the issue, such as who would need to be made aware of the issue and how.
Best of luck!
Ask a Consultant

Research the Internet
Review Critical Considerations
Select the icon from the top to receive additional
information related to the situation
Tasks
- Attend the meeting with the chief security officer.
- Consider all the factors that contribute to the challenge.
- Write a report on the threat the university faces and the response it would require from your institution.
- In your report, explain what the university should do about the vulnerability and what effect any changes required might have on the university or its students, employees, graduates, or other populations.
- Answer what the vulnerability is, how dangerous it could be, what its effects are, and how it can be countered.
- Address communication regarding the issue, such as who would need to be made aware of the issue and how.
- Do a self-review of the report with respect to the evaluation criteria mentioned in the assignment requirements.
- Submit the assignment to your instructor.