Managing Risk in Information Systems
Business Continuity Planning
Consider the following table that summarizes the elements of a BCP and a DRP. After reviewing the table, click the ACTIVITY button to attempt a simple exercise.
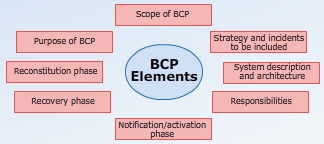
BCP
- Covers all functional areas of a business
- Ensures the entire business can continue to operate in the event of a disruption
- Involves a business impact analysis (BIA)
- Addresses other nontechnical elements of the disruption
- Focuses on getting the overall business functions back to normal
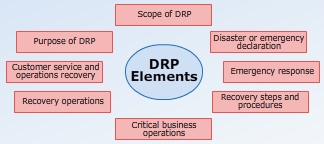
DRP
- Covers functions of only the IT department
- Includes the elements necessary to recover from a disaster
- Involves copying critical data to media or online and then moving the IT operations off-site to be recovered, if required
- Focuses on restoring and recovering IT functions
A critical eye and outside-the-box thinking must be applied to every step in BCP implementation processes. Position the mouse pointer over each step to learn more about it.
Position the mouse pointer over each role to learn more about their respective duties and responsibilities. Next, click the ACTIVITY button to attempt an exercise on roles and responsibilities.
- BCP program manager
- BCP coordinator
- BCP team leads
- Critical vendors
- Critical contractors
- Telecommuters
- Emergency management team
- Damage assessment team
- Technical recovery team
You can categorize the critical data that needs to be protected as follows. Click each categorization to learn more about it.
- Identify all equipment, such as servers, switches, and routers.
- Include databases hosted on the system.
- Include files, documents, or spreadsheets.
- Include necessary supplies.
Next, click the ACTIVITY button to attempt an exercise on best practices.
John Motorcycle Parts Scenario
You have recently bought John Motorcycle Parts—a company that sells widgets to big motorcycle companies. Your company operates on a coast threatened by hurricanes. You want to ensure that the company's Web site used for online sales of widgets continues to operate if hit by a hurricane. For this, you need to have a security plan in place. You, as the owner, have to perform the following tasks:
- Identify the risks and problems that need to be fixed before your audit team finds loopholes in your overall security plan.
- List five things that could go wrong without a BCP and a DRP.
- List five risks that need to be addressed first.
A detailed BCP will enable you to perform these tasks. You can also follow some best practices while developing a BCP. Click the RESOURCES icon to read more about these best practices.
In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Following the instructions provided in the Lab Manual, you will be able to practice the steps IT Security Specialists perform on a daily basis and develop the skills required for effective execution and management of IT Security operations.
In this section, you will have an opportunity to apply what you've learned in this lesson in the context of analyzing a business situation. Although simplified, a problem scenario provided here depicts the challenges often faced by professionals in the workplace.
In this interactive case study, you will explore a business situation, review critical information related to the problem discussed in the case, decide on the course of action, and receive a decision analysis summary that discusses the implications of your decision. Once you analyze the impact of your decision, explore alternative solutions to learn about other potential ways to address the issue in the case. Complete your work on the case by submitting the graded assignment that will reflect on your process of analyzing the business situation and defining an appropriate course of action.
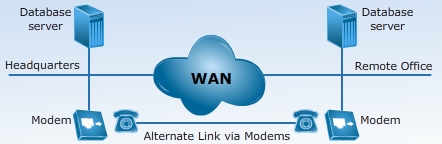
You need to develop a BCP, considering the additional information on the Health Network IT infrastructure. You will get this information from the chief network manager, who is waiting for you in the server room. Click the image of the chief network manager to know what information will be shared with you.
After you have gone through the challenge, navigate to Contributing Factors from the panel at the top of your screen.
Congratulations on your good work! Before you develop a BCP for DLIS, I have something to share with you.
DLIS has a global reach and at least 50 file servers and 12 databases running everything from an enterprise resource planning (ERP) system to the organization payroll system that has electronic funds transfer (EFT) capability. Other things worth noting are a warm site within 50 miles of the headquartersí data center. No plans exist for it. You will want to use it in planning your BCP. Currently, backups are done with an outside vendor. However, you will want to recommend a new process, a vendor, and develop a new backup plan for approximately 5 terabytes of critical classified data. Do not forget to develop a testing plan for your BCP.
You can always come to me in case of any doubts or queries. All the best.
Research the Internet
Select the icons from the top to receive additional
information related to the situation
Tasks
- Read the case scenario of Health Network.
- Understand your task for this assignment from the chief network manager in the server room.
- Consider all the factors that contribute to the challenge.
- Write the purpose of drafting a BCP.
- Explain the scope and boundaries of the BCP.
- Explain the key roles involved in the BCP and their respective responsibilities.
- Analyze and write a proposed schedule for the BCP.
- Research and summarize your backup approaches and justify your final recommendations.
- Collate all information in a Microsoft Word (or compatible) document and do a self-review.
- Submit Project Part 2 Task 2 to your instructor.