Network Security,
Firewalls, and VPNs
Network Security Basics
In this section you will examine the concepts, processes, roles, and context related to information system security issues faced by IT professionals on a daily basis, and learn why certain decisions are made in the real workplace.
Concepts:Before you can perform any task, you need to understand critical concepts being used in the IT security world. These concepts provide the relevant and cumulative framework necessary for effective learning.
Process:Processes are a part of any workplace. Business processes cut across existing organizational divisions. In this section, you will learn about the standard processes that exist in work environments today.
Roles:Most organizations are structured into divisions and departments (e.g. sales, finance, customer service, IT) that are dedicated to performing specific functions and staffed with personnel who have expertise in those functions.
Where different activities in a process require different skills, the process is likely to involve a number of people and departments. It is critical for you to learn who is involved in, or impacted by, IT security-related decisions, and how individuals in those roles communicate and collaborate with IT security professionals.
Concepts:Processes and roles vary according to industry. Contextual differences are most apparent in areas such as government, military, health care, and corporations. In this section, you will learn how IT security processes and methods are implemented in those professional contexts, and how the differences between these industries impact IT security problem resolution.
Rationale:This section of the lesson will help you with "Why?" questions. Ability to formulate a rationale, or reasoning, behind every business decision supported by data analysis is a critical competency required from today's IT security professionals. In this section, you will learn how professional decision making takes place in a real workplace environment.
- What are the fundamental concepts of network security?
- What are the primary goals of information security?
- What are the secondary goals of information security?
- What are the primary mandates of a network security policy?




Think about the uses, benefits, and limitations of the following common countermeasures. Then, position the mouse pointer over each countermeasure to read about it. After going through the countermeasures, click the ACTIVITY button to attempt a simple activity related to countermeasures.
- Firewalls
- Virtual private network (VPN)
- Intrusion detection system (IDS)
- Intrusion prevention system (IPS)
- Data loss prevention
- Security incident and event management (SIEM)
- Continuous control monitoring
- Vulnerability assessment
Click each role to read about it. Next, click the ACTIVITY button to attempt a simple activity related to roles and responsibilities.
- Senior management
- IT management
- IT security staff
- Managers (nontechnical)
- Network administrators
- Users
- Auditors?
- Business requirements considerations
- Wired networking considerations
- Wireless networking considerations
- Mobile networking considerations
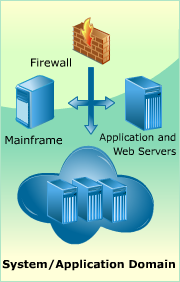
Position the mouse pointer over each domain to learn more.


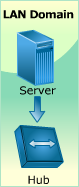
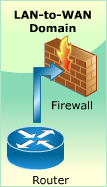









In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Following the instructions provided in the Lab Manual, you will be able to practice the steps IT Security Specialists perform on a daily basis and develop the skills required for effective execution and management of IT Security operations.
In this section, you will have an opportunity to apply what youíve learned in this lesson in the context of analyzing a business situation. Although simplified, a problem scenario provided here depicts the challenges often faced by professionals in the workplace.
In this interactive case study, you will explore a business situation, review critical information related to the problem discussed in the case, decide on the course of action, and receive a decision analysis summary that discusses the implications of your decision. Once you analyze the impact of your decision, explore alternative solutions to learn about other potential ways to address the issue in the case. Complete your work on the case by submitting the graded assignment that will reflect on your process of analyzing the business situation and defining an appropriate course of action.
Lately, you had suggested network security countermeasures to Corporation Techs. Do you think all your suggestions will be incorporated in the system, or will you need to provide a rationale for implementing each remedy? Let's find out.
Click the image of the chief security officer to know what he wants to share with you. After you have gone through the challenge, navigate to Contributing Factors from the panel at the top of your screen.
Corporation Techs plans to add a Web server and an Internet connection to the network. The Internet connection will provide Internet access to the workstations and allow customers to externally access the Web server. Additionally, Corporation Tech plans to add 10 laptops and would like to connect them to the network in wireless mode.
Corporation Techs' network team comes to you with a suggested network design and asks you to review and identify possible security threats, if any. You need to research and identify the appropriate network security countermeasures for the identified threats.
We have planned another meeting next week where Corporation Techs' board will finalize network security countermeasures that will reduce or eliminate the security threats in the suggested network design. Therefore, the board wants you to create a summary that supports your list of suggested network security countermeasures. I will send you an e-mail that will detail out what all is required in your summary.
Review Documents
Read E-Mail
Select the icon from the top to receive additional
information related to the situation
Tasks
- Have a discussion with the chief security officer.
- Consider all the factors that contribute to the challenge.
- Review the case of Corporation Techs.
- Analyze the possible security threats in the suggested network design.
- Create a summary in the form of a list of all the suggested network security countermeasures.
- Write your rationale for each suggested countermeasure.
- Prioritize your suggested countermeasures for the given challenge.
- Write your final recommendations.
- Conduct a self-review of the executive summary with respect to the evaluation criteria mentioned in the assignment requirements.
- Submit the assignment to your instructor.