Network Security,
Firewalls, and VPNs
Network Security Management
Reflect on answers to the following questions related to network security management strategies. Then, click each question to reveal its answer. After going through the answers, click the ACTIVITY button to attempt a simple activity.
- What are the common network security management strategies?
- How do training and security awareness improve network security?


Reflect on answers to the following questions related to network security assessments. Then, click each question to reveal its answer. After going through the answers, click the ACTIVITY button to attempt a simple activity.
- What are the steps involved in conducting a network security assessment?
- What is the importance of a security information and event monitoring (SIEM) tool in network security assessment?


- Nagios
- SmokePing
- GroundWork
- Ganglia
- Cacti
- Ntop
- WhatsUp Gold
- Iris
Reflect on answers to the following questions related to information security strategies. Then, click each question to reveal its answer. After going through the answers, click the ACTIVITY button to attempt a simple activity.
- What areas should an organization focus on when planning its information security strategy?
- Why is integration of firewalls and VPNs considered a good information
security strategy?



- Preparation: Select and train incident response team (IRT) members and allocate resources.
- Detection: Confirm actual breaches.
- Containment: Restrain further infection.
- Eradication: Resolve the problem.
- Recovery: Return to normal operations.
- Follow-up: Review the incident and solution to improve future responses.
In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Following the instructions provided in the Lab Manual, you will be able to practice the steps IT Security Specialists perform on a daily basis and develop the skills required for effective execution and management of IT Security operations.
In this section, you will have an opportunity to apply what you’ve learned in this lesson in the context of analyzing a business situation. Although simplified, a problem scenario provided here depicts the challenges often faced by professionals in the workplace.
In this interactive case study, you will explore a business situation, review critical information related to the problem discussed in the case, decide on the course of action, and receive a decision analysis summary that discusses the implications of your decision. Once you analyze the impact of your decision, explore alternative solutions to learn about other potential ways to address the issue in the case. Complete your work on the case by submitting the graded assignment that will reflect on your process of analyzing the business situation and defining an appropriate course of action.
Click the image of the manager to get his instructions.
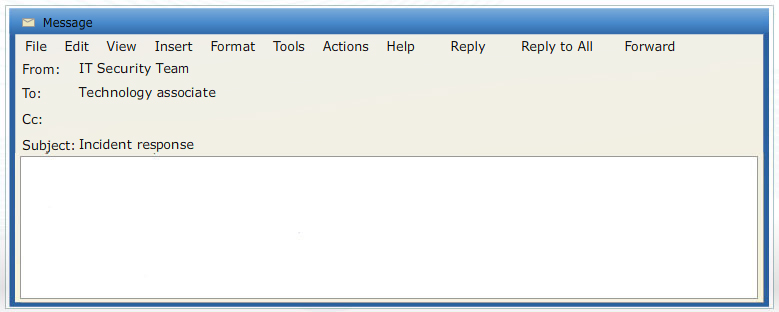
After you have gone through the challenge, navigate to Contributing Factors from the panel at the top of your screen.A firewall breach has occurred on Corporation Techs network. As a member of the IT security team, you should have received an e-mail alert. Please create a postincident follow-up report, in the form of an executive summary format, about the incident for management review. Let me know if you need any support.

Read E-mail

Review Critical Considerations
Select the icons from the top to receive additional
information related to the situation
Tasks
- Review the details of the incident and corrective action taken by the IT security team.
- Research the Internet for typical executive summary reports.
- Identify the essential elements in a typical executive summary report.
- Ensure that the report has a professional look.
- Ensure that the executive summary report is precise.
- Submit the final postincident executive summary to the instructor.