In this section, you will examine a number of topics related to cyberwarfare. You will learn about how cyberwarfare is waged and the means used for combating cyberwarfare.
Concepts: Military leaders have always realized that information is a critical part of conducting warfare. It is not surprising that cyberwarfare is simply a natural extension of traditional warfare in the digital realm (or landscape).
Objectives: The objectives of cyberwarfare are similar to those of conventional warfare—to protect one’s own private information and attempt to intercept and decipher the information of one’s adversaries.
Context: Our world has experienced momentous changes over the past few decades. You need to know how these changes have led to today’s real-world challenges in order to have a context for how cyberwarfare is conducted and combated.
Technology: Cyberwarfare involves the use of the latest developments in technology. The evolution of technology, and the technology of war, has revolutionized the way information is gathered, protected—and attacked.
Understanding: Cyberspace has become mankind’s latest battlefield. You will come away from this course with a firm understanding of the techniques used in both offensive and defensive information warfare as well as how cyberwarfare shapes military policy.
Click on each of the following items to learn more. Next, click the ACTIVITY button to complete a brief exercise.
- What is cyberwarfare?
- The likelihood of cyberwar

Click on each of the following items to learn more.
- Ancient warfare
- World wars
- Cold war
- Iraq War and weapons of mass destruction
Click on each item to learn more. Next, click the ACTIVITY button to complete a brief exercise.
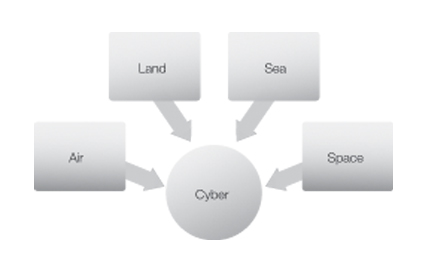
- The four traditional
domains of warfare - The early stages of
cyberwarfare - The U.S. Cyber Command
(USCYBERCOM)
Click on each of the two major categories of information operations to learn more.
- Offensive information operations
- Defensive information operations

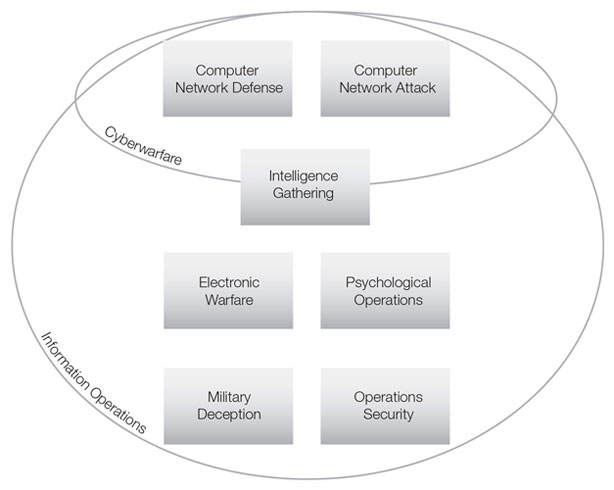
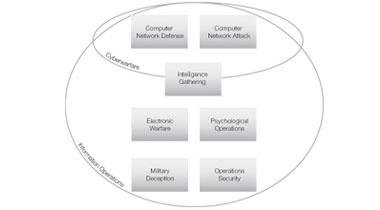
In 2003, the Department of Defense organized information operations into seven categories and made specific recommendations about how the military might better organize, train, and equip to wage information operations in the future.
The figure illustrates the relationship between the seven techniques of information operations, cyberwarfare, and information operations. In the figure, notice that:
- Computer network defense and computer network attacks fall within the realm of cyberwarfare.
- Some intelligence-gathering activities fall within the cyber domain: specifically those that use cyberespionage techniques.
- While all intelligence gathering fits within the domain of information operations, not all intelligence operations are cyberwarfare.
- Computer network attack
- Computer network defense
- Intelligence gathering
- Electronic warfare
- Psychological operations
- Military deception
- Operations security
In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Demo Lab provided in this lesson guides you through the steps needed to perform tasks related to cyberwarfare. You may review these guided interactions as many times as needed.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Follow the instructions provided in the Lab Manual.
In this section, you will have an opportunity to apply what you have learned in this lesson. A scenario is provided here that depicts the challenges often faced by professionals in the workplace.
You will explore the scenario, review related critical information, research a topic, and present your findings. Complete your work by submitting the graded assignment.
You work for General Technology Security, Inc. (GTSI). GTSI is a military contractor specializing in information systems security.
The organization is responding to a request for proposal (RFP) from the U.S. Cyber Command. The proposal will detail how and why your firm should be contracted to provide information systems security services to USCYBERCOM.
You have just attended a meeting in your firm’s conference room that discussed the RFP.
Click on your papers to read the brief of your role in preparing the RFP.
This RFP is important to our firm. I am asking each of you to be involved in our proposal.
Your particular assignment will be to research USCYBERCOM to find out more about the organization—its mission, its role in protecting our nation, and the details regarding a few of the commands that are part of USCYBERCOM (NETCOM, 1st IO Command, and INSCOM).
Thank you in advance for your effort.
Lt. Colonel Findlay, U.S. Army, retired
President and Chief Executive Officer
General Technology Security, Inc.
In this lesson, you learned that information is a military asset. You learned some of the basics of cyberwarfare and that cyberwarfare includes a wide range of activities that use information systems as weapons against an opposing force.
Research USCYBERCOM. Then write a paper that describes the organization, including its mission, its role in protecting our nation, and the role of NETCOM, 1st IO Command, and INSCOM.
For a checklist of action items, navigate to Course of Action on the right panel of the screen.
Use the following checklist as a guide to complete this assignment. Note that the tasks you have completed are already checked on the list.
- Read the verbiage of the brief from your company president.
- Consider all the factors that contribute to the challenge.
- Research USCYBERCOM.
- Write a paper that:
- Describes USCYBERCOM’s mission
- Discusses USCYBERCOM’s role in protecting our nation
- Describes the role of NETCOM, 1st IO Command, and INSCOM