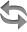Network Security,
Firewalls, and VPNs
Network Security Tools and Techniques
- Nmap and Zenmap
- Nessus
- Retina
- SAINT
Let’s look at the steps Jack follows to perform network analysis. Position the mouse pointer over each step to learn more. Next, click the ACTIVITY button to attempt a simple activity related to network analysis.
Think about answers to the following questions. Then, click each question to reveal its answer. After looking at the answers, click the ACTIVITY button to attempt a simple activity related to network analysis tools.
- What is the purpose of data loss or data leak prevention tools?
- What are the essentials of ingress and egress filtering?
- How do border routers help in protecting the LAN-to-WAN domain?
- What are some of the common network security and analysis tools?
IPS
- It monitors internal hosts or networks, watching for symptoms of compromise or intrusion.
- It acts as the first layer of proactive defense.
- It detects attempts to attack or intrudes before attacks are successful.
- On detecting an intruder, an IPS responds by stopping an attack from proceeding. Some IPS provide basic data loss or leak prevention capabilities.
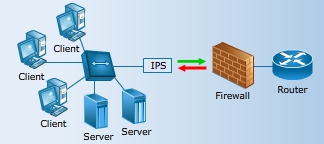
IDS
- It monitors internal hosts or networks after an attack has occurred.
- It reacts to events that the IPS misses.
- It seeks symptoms of compromise or intrusion.
- On detecting an intruder, an IDS sends commands to the firewall to break the connection, blocks an IP address, and blocks a port or protocol.
After reading about these solutions, click the ACTIVITY button to attempt a simple activity related to HIDS and NIDS.

Although HIDS and NIDS are important countermeasures against outside attacks, they have a few disadvantages:
- They require an intense tuning or training period.
- They can create a false sense of security.
- Sometimes, they consume so many resources that the system is unable to perform its primary job.
- A NIDS might experience difficulty handling encrypted network traffic.
In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Following the instructions provided in the Lab Manual, you will be able to practice the steps IT Security Specialists perform on a daily basis and develop the skills required for effective execution and management of IT Security operations.
In this section, you will have an opportunity to apply what you’ve learned in this lesson in the context of analyzing a business situation. Although simplified, a problem scenario provided here depicts the challenges often faced by professionals in the workplace.
In this interactive case study, you will explore a business situation, review critical information related to the problem discussed in the case, decide on the course of action, and receive a decision analysis summary that discusses the implications of your decision. Once you analyze the impact of your decision, explore alternative solutions to learn about other potential ways to address the issue in the case. Complete your work on the case by submitting the graded assignment that will reflect on your process of analyzing the business situation and defining an appropriate course of action.
You have been working as a technology associate in the information systems department at Corporation Techs for a while now. You are going to Las Vegas for the weekend, and you are excited about the trip. While you are thinking about the trip in the break room, your manager comes in and says a big task has been planned for you. Hiding your feelings, you smile and ask, “What’s the big task?” Click the image of the manager to get instructions.
After you have gone through the challenge, navigate to Contributing Factors from the panel at the top of your screen.All the best!

Attend a Meeting

Read E-Mail

Research the internet
Select the icon from the top to receive additional
information related to the situation
Tasks
- Analyze the saved Nmap or Zenmap scan of a Web server host.
- Identify services that were detected on the system.
- Research the use of each service.
- Determine which services are unnecessary.
- Create a report detailing your plan and support your conclusions.