Network Security,
Firewalls, and VPNs
VPN Fundamentals
A VPN makes a secure network connection over a public telecom infrastructure, such as the Internet, to provide remote access to private networks. A VPN enables organizations to privately transmit sensitive data remotely over public networks.
Think about answers to the following questions. Then, click each question to reveal its answer. Then, click the ACTIVITY button to attempt a simple exercise related to the limitations of a firewall.
- What are the advantages of a VPN?
- What are the disadvantages of a VPN?
- What are the various types of architecture for a VPN connection?
- What security and privacy issues are associated with a VPN?
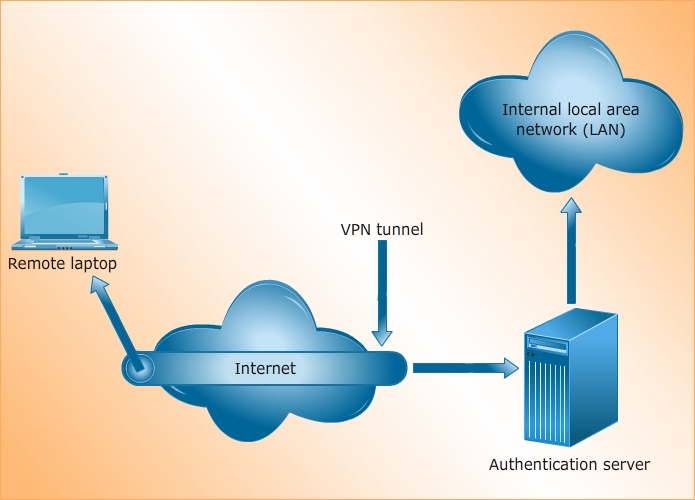

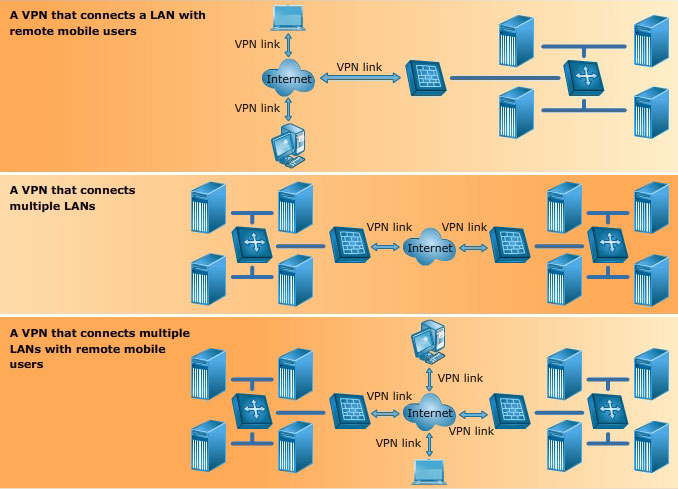


The following steps are involved in defining an effective VPN policy:
- Define enterprise-class security considerations.
- Define users, groups, and access rights.
- Create VPN-specific standards, guidelines, and procedures.
- Define VPN usage concerns and models.
Click the RESOURCES icon to learn more about each of the steps.
- Hardware-based VPNs
- Software-based VPNs
- Owned and outsourced VPNs
- Tunnel-mode VPN
- Transport-mode VPN
- Cryptographic protocols
- Network protocols
- VPN authentication, authorization, and accountability mechanisms
- What is the purpose of various VPN deployment models?
- What are the security requirements for various VPN hardware devices?
- What are the security characteristics of VPN architecture?
- What are common VPN supporting services and protocols?




In this section, you will have an opportunity to practice the concepts and processes that you have explored in this lesson.
The Hands-On Lab provides you with an engaging learning experience that is diagnostic and flexible. Following the instructions provided in the Lab Manual, you will be able to practice the steps IT Security Specialists perform on a daily basis and develop the skills required for effective execution and management of IT Security operations.
In this section, you will have an opportunity to apply what you’ve learned in this lesson in the context of analyzing a business situation. Although simplified, a problem scenario provided here depicts the challenges often faced by professionals in the workplace.
In this interactive case study, you will explore a business situation, review critical information related to the problem discussed in the case, decide on the course of action, and receive a decision analysis summary that discusses the implications of your decision. Once you analyze the impact of your decision, explore alternative solutions to learn about other potential ways to address the issue in the case. Complete your work on the case by submitting the graded assignment that will reflect on your process of analyzing the business situation and defining an appropriate course of action.
Click the image of the manager to get his instructions.
After you have gone through the challenge, navigate to Contributing Factors from the panel at the top of your screen.

Read E-mail

Review Documents
Select the icons from the top to receive additional
information related to the situation
Tasks
- Consider the advice of the chief security officer.
- Review the VPN troubleshooting information.
- Identify the relevant steps involved in the VPN connectivity troubleshooting process.
- Create the VPN connectivity troubleshooting checklist.
- Submit the checklist to your instructor.